
The goal of this publication is to help you in the development of your device with a focus on a very hot topic: Cybersecurity. With the content of this publication, you will be able to understand how Cybersecurity (also called software security) can impact your process of development and the design of your device.
Introduction
For introduction content, refer to the Part 1 previously published.
Software lifecycle security process
Software security must be under control from the beginning of the realization of the product to its end of life. It must consider the developed components as well as the integrated third-party components and their environment of use.
Software security management activities must be applied at all stages of the development and distribution of your medical device. A procedure for software security management must be developed and a software security management plan must be established for each project. Activities involved in this procedure are illustrated in the next figure and will be used to structure the content of this publication.
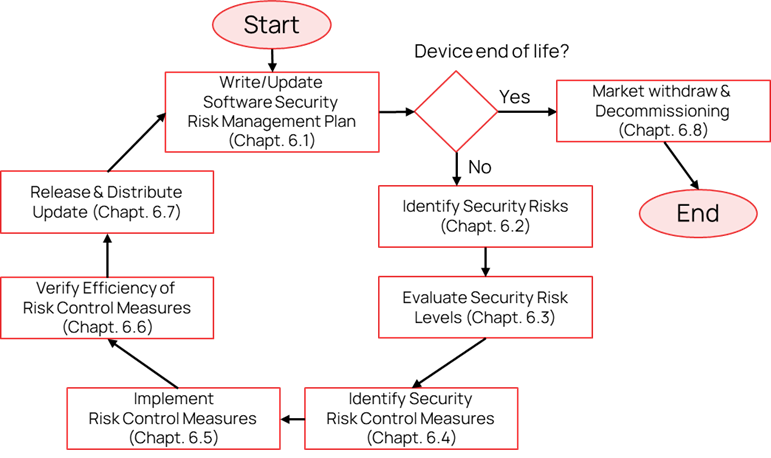
Figure 1. Security risk management process flow-chart
For each of these activities, the work to be executed depends on the phase of your project. As a reminder, the typical phases of the development and marketing of a medical device are illustrated in the next figure.
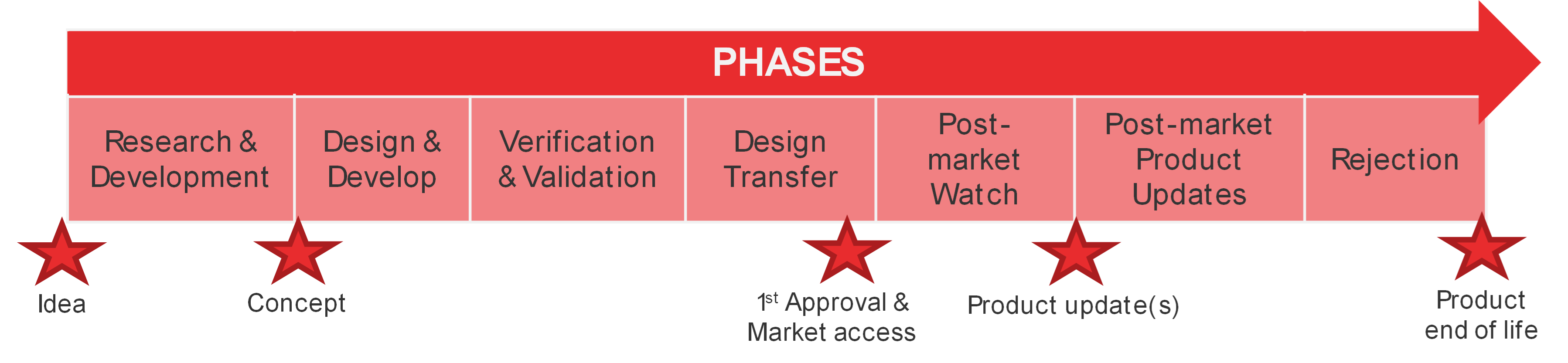
Figure 2. Medical Device development and marketing phases
In parallel of the application of this flowchart you will have to keep up to date the list of files you generate to document your software security management activities. This is usually done within the Design History File of your project. A method, usually well appreciated by reviewers is to use tags within your Design History File to quickly identify files associated with your software security management activities.
In addition, at each transition from one phase to another, you must document the files and activities you carried on in the previous phase and demonstrate the completeness of your work and the non-ambiguity and consistency of the content elaborated in the different files. This is usually performed through gate or phase reviews.
Debiotech recommends to:
- Early in your development process, describe your procedure for software security risk management,
- Refer your software security procedure in your design and development procedure and describe for each phase of your D&D procedure the applicable activities of the software security procedure,
- Based on the software security risk management procedure, create the software security risk management plan for your project,
- Using gate or phase reviews of your D&D procedure, document the activities and the files related to software security risk management,
- Keep up to date your Design History File with the files related to software security risk management.
Write/Update Software Security Risk Management Plan
Your activities for security risk management must be clearly identified and integrated within your project plan. You can have a specific document to describe your security risk management plan or integrate it into the project plan. This document allows you to illustrate your planned activities, to document assigned resources and expected timing and finally to demonstrate the completeness of your approach in the handling of security risk management aspects. Your plan is a living document that must be kept up to date. Change of plans are normal, especially in early-stage projects but lack of, or clearly inaccurate plans, will be challenged by reviewers. The Figure 8 illustrates typical activities to be included within your security risk management plan.
Debiotech recommends you to:
- Write down your Security risk management plan at the beginning of the project even if you lack visibility on its mandatory content.
- Keep it simple and high level. Details can come with other documents. The importance is to document the different activities you will have to perform at the different phases of your project, to establish a timeline and assign resources.
- Preparing a template security risk management plan (or a template of project plan integrating security risk management plan) as a complement to your Design & Development procedure is a good way to ensure its use and existence for each project you will launch. However, the filling of this template to generate a plan specific to your project is necessary.
Keep it up to date to ensure your plan is realistic.

Figure 3. Illustration of a software security risk management plan
Authors
 |
Rémi Charrier Business Development Director r.charrier@debiotech.com |
||
|
João Budzinski |
 |
||
 |
Laurent Colloud Software Project Manager l.colloud@debiotech.com |
||
|
Gilles Forconi |
 |
Next steps
Debiotech is glad to have the opportunity to share its knowledge with innovative companies from the MedTech industry. Your feedbacks on this publication are welcome and will be used to update it or to create new publications on topics you care about.
Continue your education on medical device development by:
- Accessing Debiotech historic publications: https://www.debiotech.com/news-grid/
- Following Debiotech on LinkedIn to be notified on new publications: https://www.linkedin.com/company/debiotech-sa
- Contacting us to ask a question or request personalized support: contact@debiotech.com
Debiotech would be proud to be your partner and support you with:
- Medical device design & development services:
- Software: Digital Health, Firmware, Embedded, SaMD
- Electronics: Design, Verification and Validation
- Mechanics: Design for micro-fabrication & fluidics systems
- Supply chain development and optimization
- Support in medical innovation management:
- Market analysis and segmentation
- IP management
- Business plan consolidation
- Partnership development


